Reduce the risk of information leakage
Improved security level through fraud deterrence measures
Integrated security operations
Integrated management is achieved through enhanced authentication and log management
Increased productivity
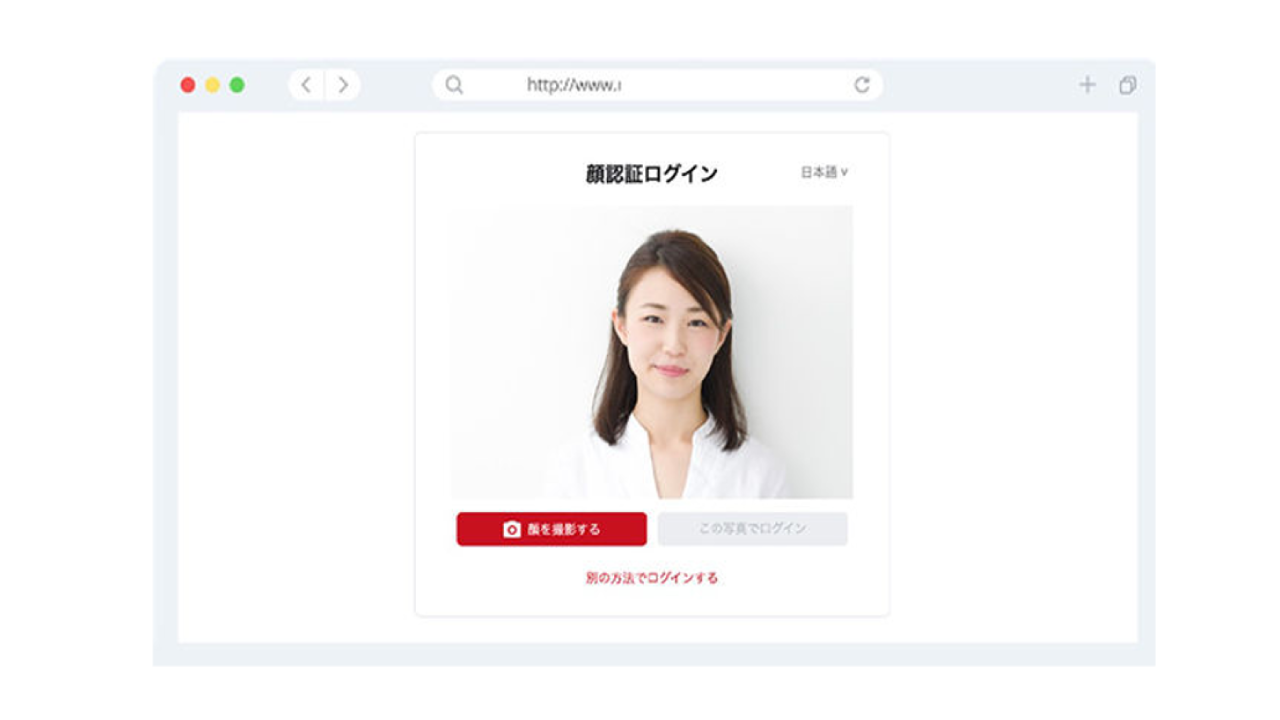
Authentication process that brings convenience and comfort
Passwordless Authentication & Solutions
A sign-on service that supports SAML and Microsoft Windows.
Provides secure passwordless authentication as a solution JCV Face Login.
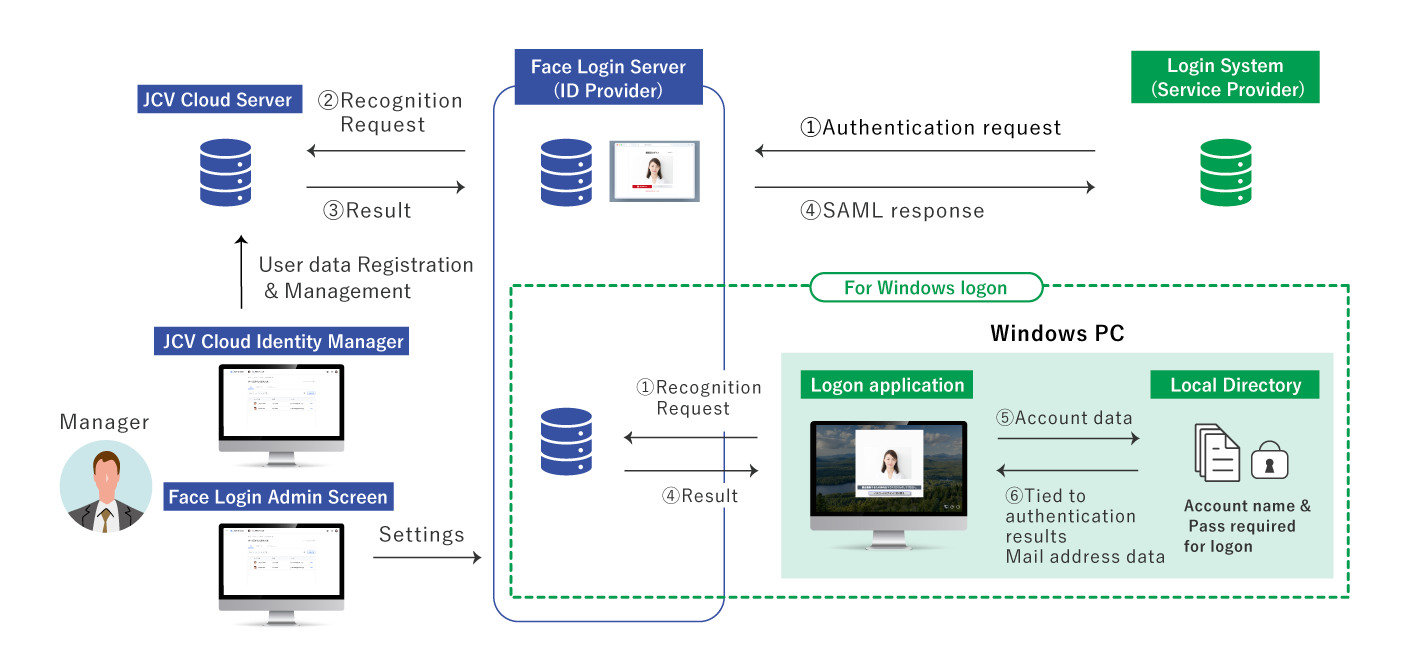
Main Functions
Settings
- Authentication flow setting
- Security policy setting
- IDP metadata download
Client Management
- Add, retrieve, delete, and update clients
- Manual mode or upload of SAML SP metadata
- Reset a temporary password for a registered identity
Documents
You will find detailed information on features, usage, quick start, and more.
Download EXE Installer for Windows Logon