The Power of Recent Facial Recognition
Modern facial recognition is a game-changer. Forget about the old-schooled technology that breaks when you wear glasses. It now can see through obstacles like makeup and masks and even tell identical twins apart. Backing its rise, it is estimated to be worth $5.15 billion in 2022 and is set to grow at a 14.9% rate each year until 2030.
What about liveness detection and why
So this is why liveness detection is crucial. Think of someone using a photo of your face to deceive a facial payment system connected to your bank. Liveness detection can prevent this from happening. In most scenarios, skipping liveness detection is as risky as having an account without a password.
Liveness detection is like the security code on the back of your credit card, only more powerful. Nowadays it utilizes a variety of different method, from ultra-red rays to the pulse of your arteries and veins.
Tools and Resources
Can’t wait to explore the full spectrum of facial recognition? Checkout some examples or dive into this interactive demo that includes everything from face detection to liveness and attributes: Face Recognition Interactive Demo
For those more technically inclined, the Model Explorer is a gateway to understand the nuances and performance metrics of various face recognition models. And guess what? It's free! No hidden costs or credit card needed.
Understanding the Different Types of Face Recognition Attacks
The ISO Standard – ISO 30107
As someone well-versed in cybersecurity, you might wonder: How can every potential attack vector be tested? Surely there are some strange spoofing techniques that you never thought about. Don’t worry, ISO has you covered. The ISO 30107 is an international standard that serves as the touchstone for Biometric presentation attack detection. Feel free to download the standard and examine it yourself, but here are a few attacking method pickups for you.
Common face recognition attacking method
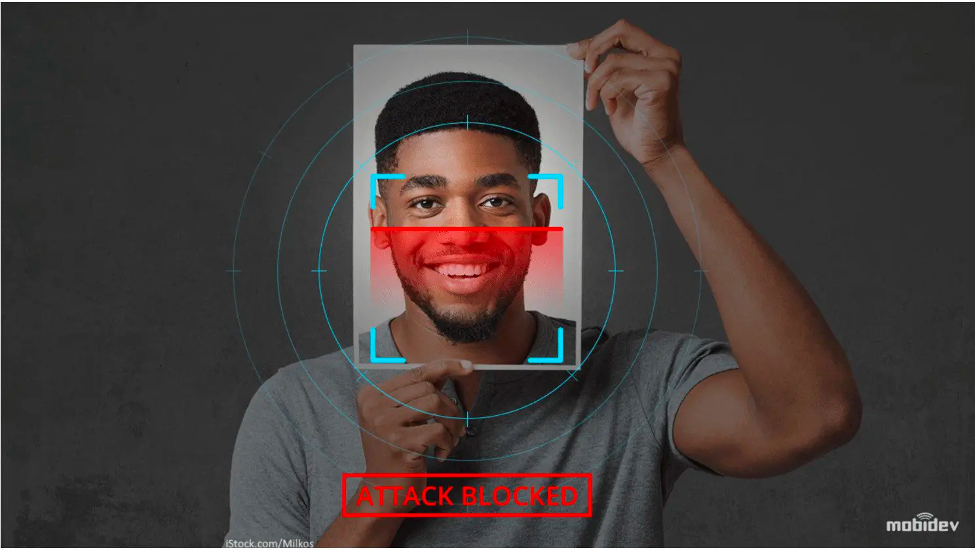
Print Out | The age-old trick of printing the victim's face and presenting it to the camera. Elementary and easily defended. However it also has the most variation, and high-resolution print-outs may look very realistic on photographic papers. (Fig. 1-1)
Colored Print-Out | This method deserves a special mention: By giving print-outs some base color, this attack can mimic facial textures enough to cheat through many detectors. (Fig. 1-2)

2D Mask | Crafting a mask using a printed photograph, sometimes even cutting out features to give it a more 3D appearance. The attacker will hold the mask close to the attacker’s own face. This has the advantage of passing interactive liveness checks that ask you to perform certain motions. For example, tasks like blinking or rotating your head will be penetrated by this attack. (Fig. 2)

T-Crop | A variant of the 2D mask where only prominent features like eyes and nose are used. The idea comes from most face recognizers recognizing faces based on these features. The closer the colors match, the harder it is to detect this attack. (Fig. 3)

Display & Replay Attacks | A display attack uses screens (probably from smartphones) to display static images of the attacking face. Replay attack shows a video of the attacking face, which is helpful when dealing with multi-frame liveness detectors.
3D Mask | 3D masks are high-end attacks (often seen in movies) that involve scanned models of the attacking face, made from various materials, and could easily cost up to thousands of dollars to produce one. (Fig. 4)

Deep Fake | The sophisticated tech that hacks the device's camera, overlaying the victim's face with another, almost seamlessly. Its detection mandates an entirely different set of techniques, recognized by the ISO standard.
Here is a quick recap and organization of some of the most common attack methods.